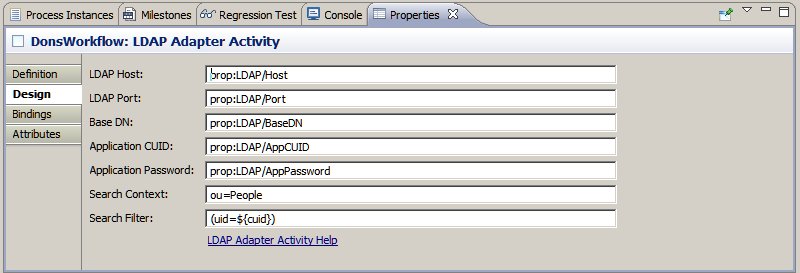
| Symbol |
Description |
| & |
conjunction (i.e., and -- all in list must be true) |
| | |
disjunction (i.e., or -- one or more alternatives must be true) |
| ! |
negation (i.e., not -- the item being negated must not be true) |
| = |
equality (according to the matching rule of the attribute) |
| ~= |
approximate equality (according to the matching rule of the attribute) |
| >= |
greater than (according to the matching rule of the attribute) |
| <= |
less than (according to the matching rule of the attribute) |
| =* |
presence (i.e., the entry must have the attribute but its value is irrelevant) |
| * |
wildcard (indicates zero or more characters can occur in that position); used when
specifying attribute values to match |
| \ |
escape (for escaping '*', '(', or ')' when they occur inside an attribute value) |